Automated S3 Security: Lambda Functions to the Rescue
By Saumil Shah, Khushi Carpenter, Piyush Jalan / Jul 18, 2023
ABSTRACT:
In today's business landscape, the widespread migration of workloads to the cloud has become a norm, with S3 playing a crucial role as a key solution for effective data storage and retrieval. Further, ensuring the security of S3 buckets becomes paramount. In this technical blog, we will explore an automated approach to enhance the security of S3 buckets using AWS Lambda. By leveraging CloudTrail events and Lambda functions, we can detect and remediate common security issues related to S3 public access block.
POTENTIAL SECURITY THREATS OF S3
Amazon S3 is widely used for static website hosting, providing scalability and cost-effectiveness. However, disabling the public access block exposes security threats. Without the block, misconfigurations or errors in permissions can lead to unintended public access, potentially exposing sensitive information. Unauthorized listing of bucket contents becomes possible, giving attackers insights for further exploitation.
SECURITY RISK OF S3:
- Disabling the public access block exposes security threats
- Misconfigurations or errors in permissions can lead to unintended public access
- Unauthorized listing of bucket contents becomes possible, enabling further exploitation
- Inadvertent changes to block settings can bypass security measures
- Failure to enforce encryption increases the risk of exposing sensitive data at rest
- Misconfigured access control policies may allow unauthorized public access
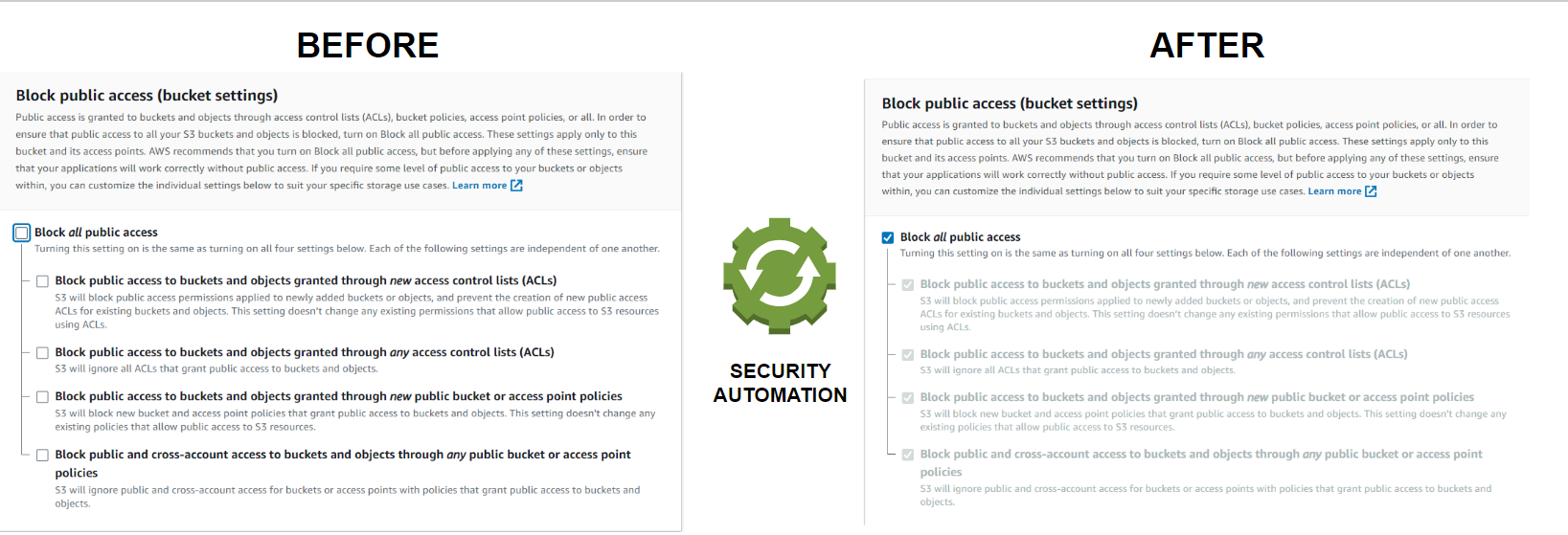
Thus, Regular security audits are essential to identify changes or misconfigurations. Inadequate auditing could lead to undetected vulnerabilities. To reduce the risk of these threats, it is essential to have an automated system that regularly checks the environment to ensure that critical controls are enabled for the specific use case.
AUTOMATED SECURITY REMEDIATION WITH LAMBDA AND EVENT BRIDGE
Let's explore a practical example of restricting public access to S3 buckets.
Here is the architecture we will be implementing to address the issue at hand.
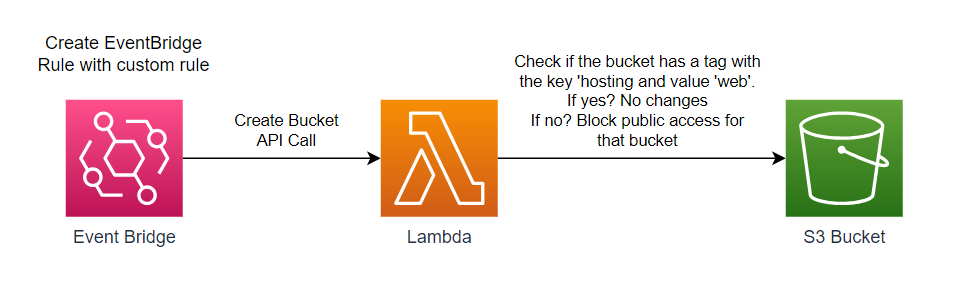
The lambda function is designed to be triggered by the ‘CreateBucket’ event in CloudTrail. Its purpose is to block public access for S3 buckets that do not have a specific tag. The tag, with the key "hosting" and the value "web," is crucial for identifying buckets which are used for static website hosting or not. By filtering based on this tag, we can ensure that blocking public access only applies to the appropriate buckets.
To begin the implementation, we will create an Event Bridge rule, which will be used for invoking a Lambda Function.
Step 1: Create below Lambda Function with Python runtime:
import boto3
def lambda_handler(event, context): s3 = boto3.client('s3') # Get all the S3 buckets response = s3.list_buckets() buckets = response['Buckets'] # Iterate through each bucket for bucket in buckets: bucket_name = bucket['Name'] try: # Get the bucket tags response = s3.get_bucket_tagging(Bucket=bucket_name) if 'TagSet' in response: tags = response['TagSet'] # Check if the bucket has the required tag has_hosting_tag = any(tag['Key'] == 'hosting' and tag['Value'] == 'web' for tag in tags) # If bucket does not have the required tag, block public access if not has_hosting_tag: s3.put_public_access_block( Bucket=bucket_name, PublicAccessBlockConfiguration={ 'BlockPublicAcls': True, 'IgnorePublicAcls': True, 'BlockPublicPolicy': True, 'RestrictPublicBuckets': True } ) except: # Handle exception print("TagSet not ") return { 'statusCode': 200, 'body': 'Public access blocked for buckets without the "hosting:web" tag' }
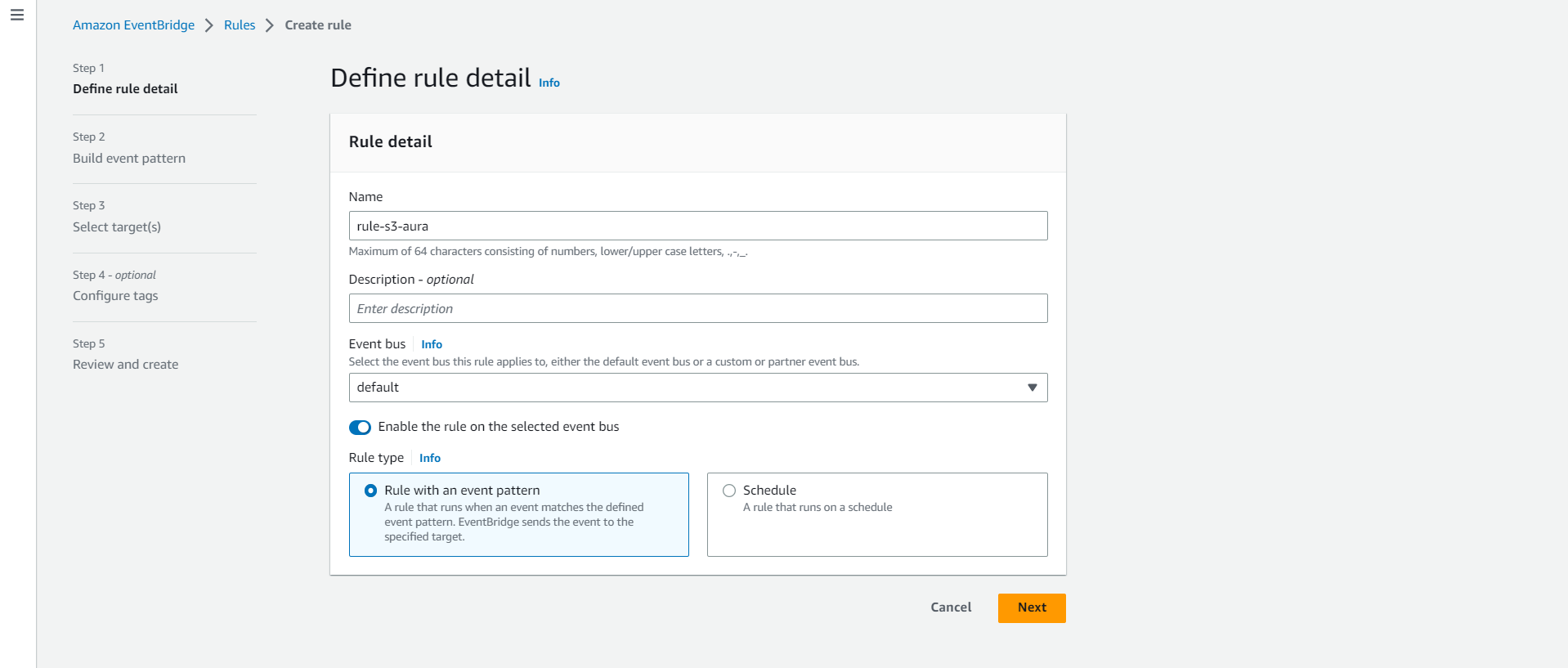
Step 2: Create the below event bridge rule with custom pattern:
-
Go to EventBridge console, create a new rule, and select rule type as event pattern:
-
In build event pattern keep everything default except ‘Creation Method’ select Custom pattern (JSON editor) in that place the event JSON code
{"source": ["aws.s3"],"detail-type": ["AWS API Call via CloudTrail"],"detail": {"eventSource": ["s3.amazonaws.com"],"eventName": ["CreateBucket"]}} -
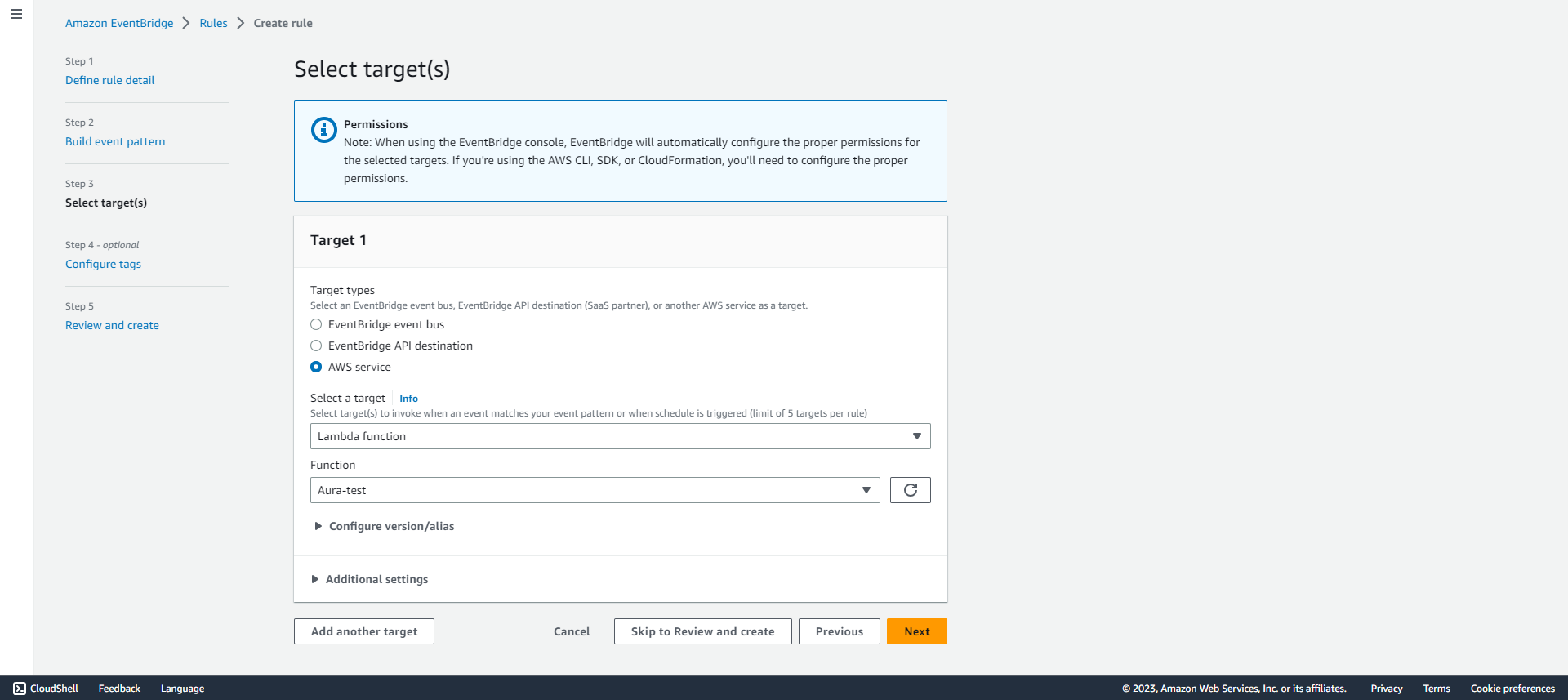
Select target as the Lambda function which was created in step 1.
-
Review and create the event bridge rule.
Note: Ensure that there is at least one CloudTrail event running in your AWS account for successful execution of the task.
CONCLUSION
In this technical blog, we delve into an automated method that utilizes AWS Lambda to bolster the security of S3 buckets. By leveraging CloudTrail events and Lambda functions, the blog demonstrates how to identify and resolve prevalent security concerns associated with S3 public access blocks. The blog covers the creation of an EventBridge rule, which serves as the trigger for invoking a Lambda function.




