Configure Ansible for Windows and Linux Instances on AWS
By Khushi Carpenter & Piyush Jalan / Apr 01, 2024
Table of Contents:
- Introduction
- Basic AWS Configuration
- Setting up Ansible on Linux
- Setting up Ansible on Windows
- Testing Ansible Setup
- Conclusion
Introduction
Ansible is a powerful open-source automation tool that aims to simplify configuration management, enhance application deployments, and automate diverse IT tasks. This technical guide offers a detailed walkthrough for integrating Windows on AWS with Ansible. The setup process entails configuring both Windows and Linux systems to facilitate Ansible management.
To ensure optimal functionality, it is crucial to designate a Linux system as the control node. This control node acts as the orchestrator, overseeing the configuration and management of the Windows host through Ansible. This approach ensures a smooth and effective automation workflow.
Basic AWS Configuration
As a prerequisite, create two instances on AWS:
- Windows Instance: This instance will serve as the target Windows host that Ansible will manage.
- Linux Instance: The Linux instance will act as the Ansible control node, orchestrating tasks on the Windows host.
Security Group Configuration for Windows
In the context of the Windows instance's security group, it's important to allow specific inbound traffic to facilitate communication with the Linux control node running Ansible. Specifically, it should allow traffic on the following ports:
- Port 5986 (WinRM over HTTPS): This port is essential for secure communication between Ansible and the Windows host.
- Port 5985 (WinRM over HTTP): While this port is optional, it's not recommended for production use due to its lack of encryption.
By configuring the security group in this manner, you ensure that the Linux control node can communicate with the Windows host over the WinRM (Windows Remote Management) protocol, facilitating Ansible management tasks.
With the AWS and security group configurations in place, it is ready to proceed with setting up Ansible on both the Linux control node and the Windows host. This will enable to harness the full power of Ansible's automation capabilities for managing the Windows infrastructure.
Setting up Ansible on Linux
The Linux server will function as the control node for Ansible, serving as the central management point for managing infrastructure and orchestrating automation tasks. Ansible will be installed and configured on this server, allowing it to define and execute automation tasks across a network of machines, including other servers, networking devices, and cloud instances.
As the control node, the Linux server will store Ansible playbooks (automation scripts) and inventory files (lists of managed nodes), and it will communicate with managed nodes using WinRM for Windows systems. Follow below steps for setting up Ansible on Linux node:
- Install ansible using below command:
pip3 install ansible
Check the version of the ansible:

- Update the inventory file using following command:
sudo vim /etc/ansible/ansible.cfg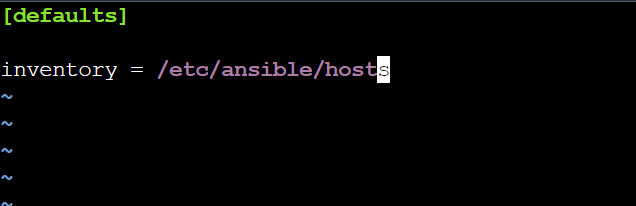
- Update the host file with the variables as shown in the image.
sudo vim /etc/ansible/hosts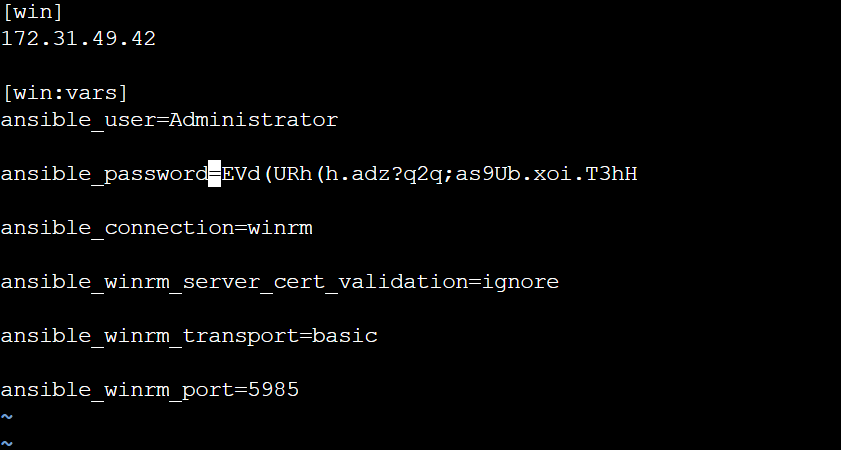
- Install winrm on the server to effectively communicate with the windows server.
pip3 install pywinrm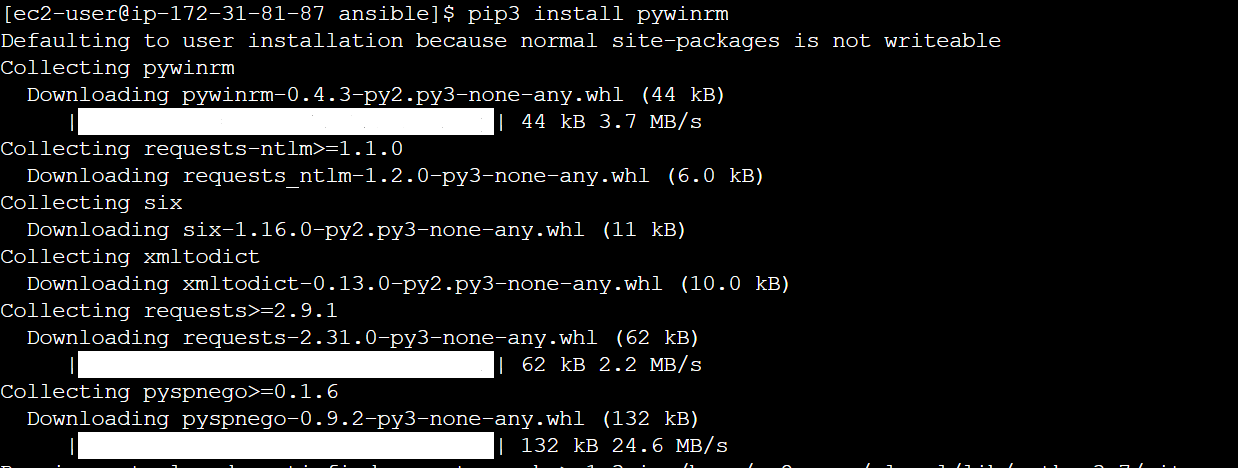
- Uninstall urllib3 and install urllib3 with version < 2.0
pip3 uninstall urllib3
pip3 install ‘urllib3<2.0’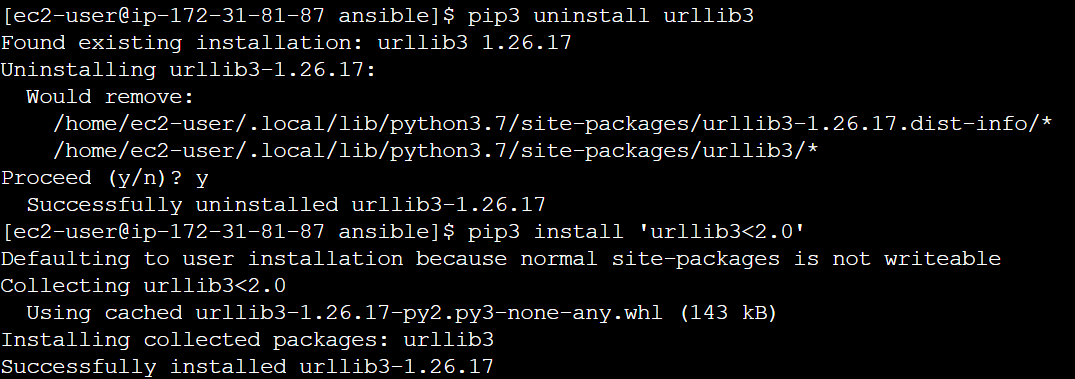
Setting up Ansible on Windows
The Windows Server will serve as the target node for Ansible, meaning it will be the system that Ansible interacts with and manages using its automation scripts. Ansible will connect to the Windows Server over the network using WinRM (Windows Remote Management) protocol to execute tasks, deploy software, configure settings, and perform other administrative actions on the Windows Server. The Windows Server must be properly configured to allow Ansible to connect to it via WinRM, and Ansible must have the necessary permissions and credentials to access and manage the Windows Server. Follow below steps for the setup.
- Login to the Windows EC2 Machine using RDP.
- Check powershell version using below command:
$PSVersionTable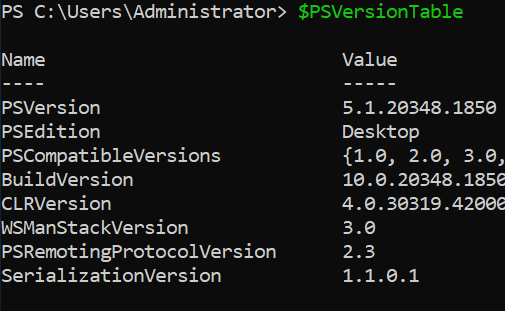
- If the version is less than 3.0 run following commands to upgrade the powershell.
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12 $url = "https://raw.githubusercontent.com/jborean93/ansible-windows/master/scripts/Upgrade-PowerShell.ps1" $file = "$env:temp\Upgrade-PowerShell.ps1" $username = "Administrator" $password = "Password" (New-Object -TypeName System.Net.WebClient).DownloadFile($url, $file) Set-ExecutionPolicy -ExecutionPolicy Unrestricted -Force &$file -Version 5.1 -Username $username -Password $password -Verbose Set-ExecutionPolicy -ExecutionPolicy RemoteSigned -Force $reg_winlogon_path = "HKLM:\Software\Microsoft\Windows NT\CurrentVersion\Winlogon" Set-ItemProperty -Path $reg_winlogon_path -Name AutoAdminLogon -Value 0 Remove-ItemProperty -Path $reg_winlogon_path -Name DefaultUserName -ErrorAction SilentlyContinue Remove-ItemProperty -Path $reg_winlogon_path -Name DefaultPassword -ErrorAction SilentlyContinue - In PowerShell v3.0, a bug restricts the memory available to the WinRM service. To address this issue, utilize the Install-WMF3Hotfix.ps1 script to apply a hotfix on affected hosts. Failure to install this hotfix may result in Ansible being unable to execute certain commands on the Windows host.
To install the hotfix:
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12 $url = "https://raw.githubusercontent.com/jborean93/ansible-windows/master/scripts/Install-WMF3Hotfix.ps1" $file = "$env:temp\Install-WMF3Hotfix.ps1"Run the below command to execute the script:
(New-Object -TypeName System.Net.WebClient).DownloadFile($url, $file) powershell.exe -ExecutionPolicy ByPass -File $file -Verbose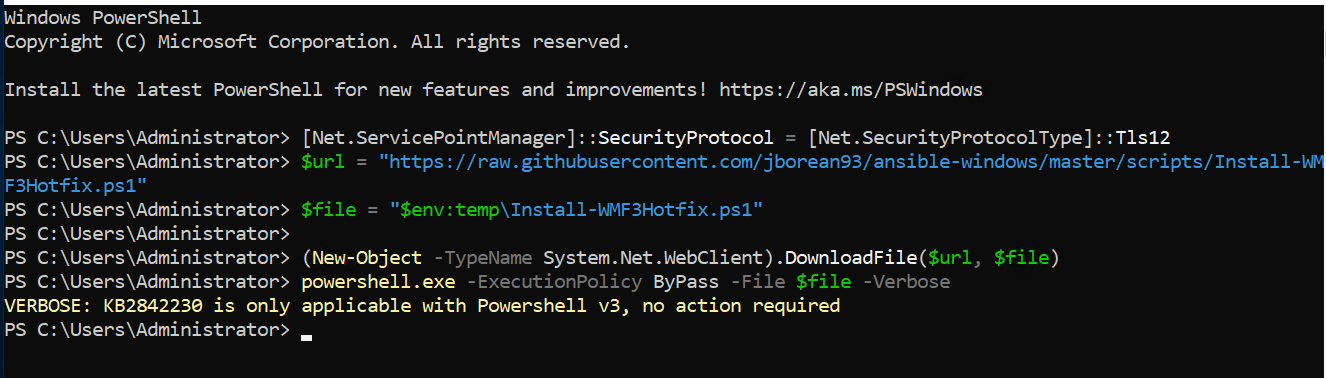
- Setup WinRM:
It is necessary to configure the WinRM service to facilitate connectivity with Ansible. The WinRM service comprises two primary components that dictate how Ansible can interact with the Windows host: the listener and the service configuration settings.
Setup WinRM Listener
- The WinRM service listens for requests on designated ports, each requiring a created and configured listener. To review the existing listeners active on the WinRM service use below command:
winrm enumerate winrm/config/Listener
- Setup the listener using winrm quickconfig for HTTP

Setup WinRM Service
- WinRM service component's behavior, including authentication options and memorysettings could be managed. To retrieve a list of the current service configuration options, execute the following command:
winrm get winrm/config/Servicewinrm get winrm/config/Winrs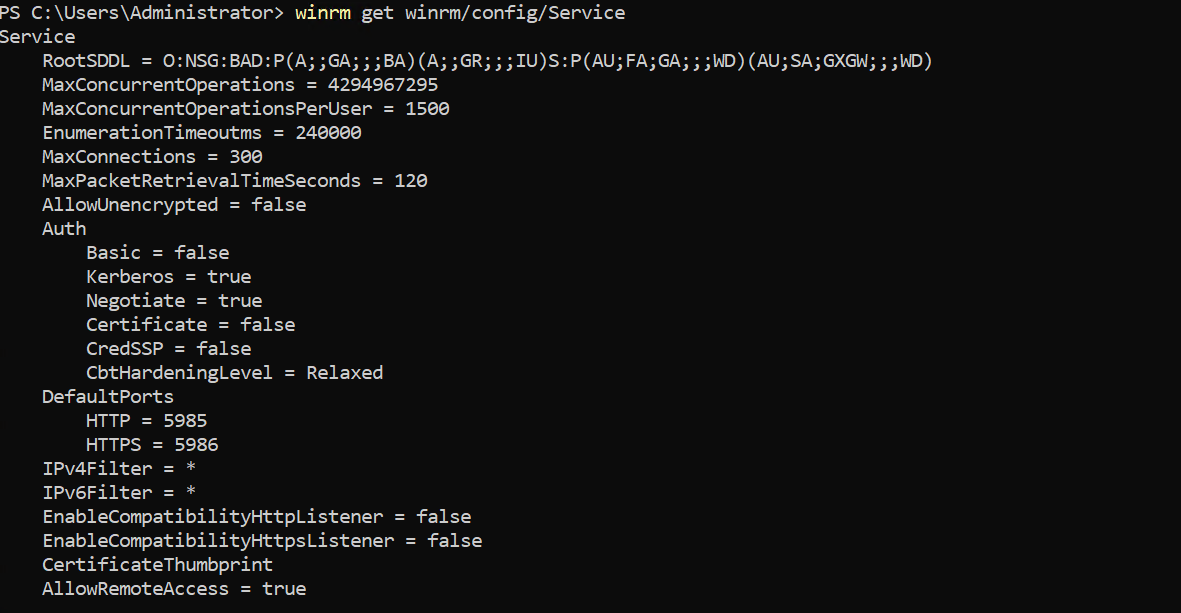

While most options do not require modification, several key settings are worth noting:
- Service\AllowUnencrypted: Specifies whether WinRM permits HTTP traffic without message encryption. Message-level encryption is only possible when the `ansible_winrm_transport` variable is set to `ntlm`, `kerberos`, or `credssp`. By default, this is `false`, and it should only be set to `true` for debugging WinRM messages.
- Winrs\MaxShellRunTime: Defines the maximum time, in milliseconds, that a remote command is permitted to execute.
- Winrs\MaxMemoryPerShellMB: Specifies the maximum amount of memory allocated per shell, including its child processes.
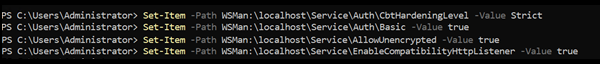
- To adjust a setting within the Service key using PowerShell, you must specify the path to the option after `winrm/config/Service`:
Set-Item -Path WSMan:\localhost\Service\AllowUnencrypted -Value true Set-Item -Path WSMan:\localhost\Service\EnableCompatibilityHttpListener -Value true Set-Item -Path WSMan:\localhost\Service\Auth\CbtHardeningLevel -Value Strict Set-Item -Path WSMan:\localhost\Service\Auth\Basic -Value true
- The WinRM service listens for requests on designated ports, each requiring a created and configured listener. To review the existing listeners active on the WinRM service use below command:
- Turn off firewall setting for Windows
Testing Ansible Setup
To check the connectivity for the setup, execute the following command:
ansible win -m win_ping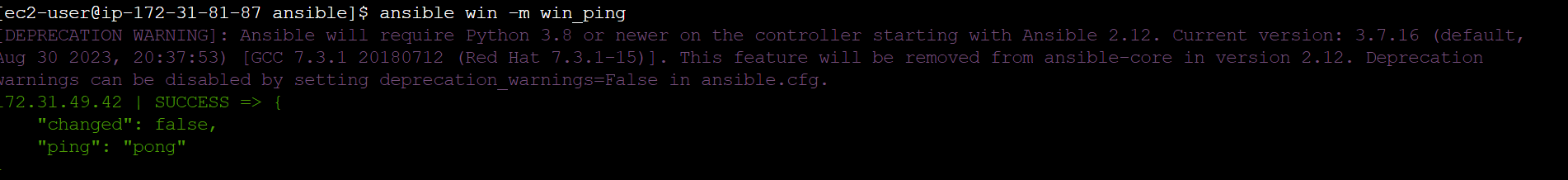
Conclusion:
Integrating Windows instances on AWS with Ansible provides a powerful automation solution for managing diverse IT tasks. By designating a Linux control node and configuring the necessary security groups and WinRM settings, which can seamlessly orchestrate automation workflows across Windows and Linux systems. This technical guide has outlined the setup process for both Linux and Windows, ensuring that Ansible can effectively manage Windows hosts on AWS. With Ansible's capabilities, configuration management can be streamlined, enhance application deployments, and automate various IT operations, ultimately improving efficiency and scalability in the cloud-native environment.




