Securing Multi-VPC Connectivity with AWS Transit Gateway
By Rinku Nayagpara / Sep 20,2023
Introduction
AWS Transit Gateway is a powerful service that centralizes and streamlines network communication between on-premises networks, other AWS services, and Amazon Virtual Private Clouds (VPCs). However, network security must be implemented to protect against threats, preserve data privacy, and prevent unwanted access. Transit Gateway offers a scalable and effective approach to connecting networks. This blog post will discuss recommended methods for implementing network security in AWS Transit Gateway and offer a practical illustration of how to secure a multi-VPC environment.
Understanding AWS Transit Gateway
AWS Transit Gateway is a highly scalable service that connects several VPCs, on-premises data centers, and distant networks by serving as a hub. Transit Gateway acts as a central hub for traffic routing between various networks, eliminating the need for complex peering arrangements between different VPCs. This can save organizations time and money on network administration, and it can also improve the security and performance of their networks.
Setting up Security with AWS Transit Gateway
Assume that the Transit gateway and VPCs are already set up and security measures are to be added.
1. Set up Routing
Routes play the most basic role in granting and preventing communication between VPCs. It is recommended to set up the routing manually rather than default to limit the communications within VPCs.
Consider having a central resource hosted in VPC A that needs to be accessed by different services hosted in VPC B and VPC C. However, VPC B and VPC C should remain isolated from each other due to security or compliance reasons. In such cases, using separate route tables for attachments can fulfil the requirement.
Route Table associated with VPC A attachment.
|
Destination |
Target |
Route Type |
|
VPC B CIDR |
Attachment for VPC B |
Propagated |
|
VPC C CIDR |
Attachment for VPC C |
Propagated |
Route Table associated with VPC B and VPC C attachment.
|
Destination |
Target |
Route Type |
|
VPC A CIDR |
Attachment for VPC A |
Propagated |
Use AWS Identity and Access Management (IAM) to control access to the Transit Gateway resources only by authorized identities.
Consider an organization setup that includes transit gateway for AWS to On-prem connectivity. In this case, set up IAM using IAM user group such that only netsec administrator, and working netsec team has editing access for any kind of changes related to the transit gateway.
Consider these user groups: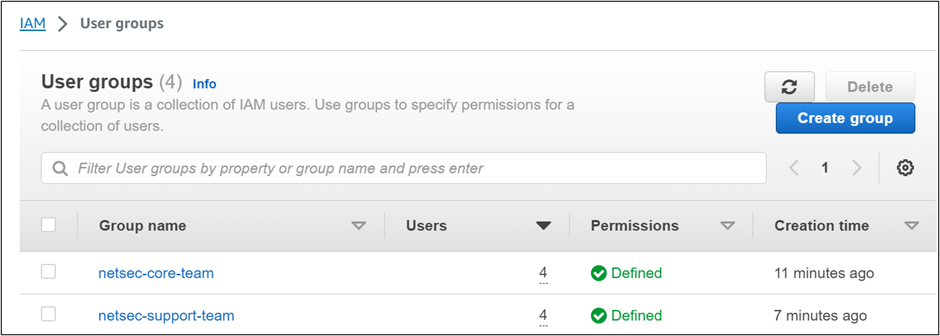
The netsec core team will have edit access over the transit gateway.
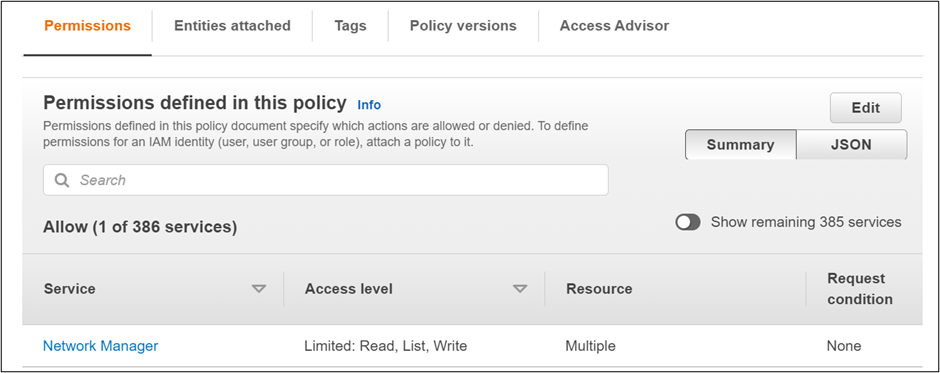
The netsec support team will have viewer access only.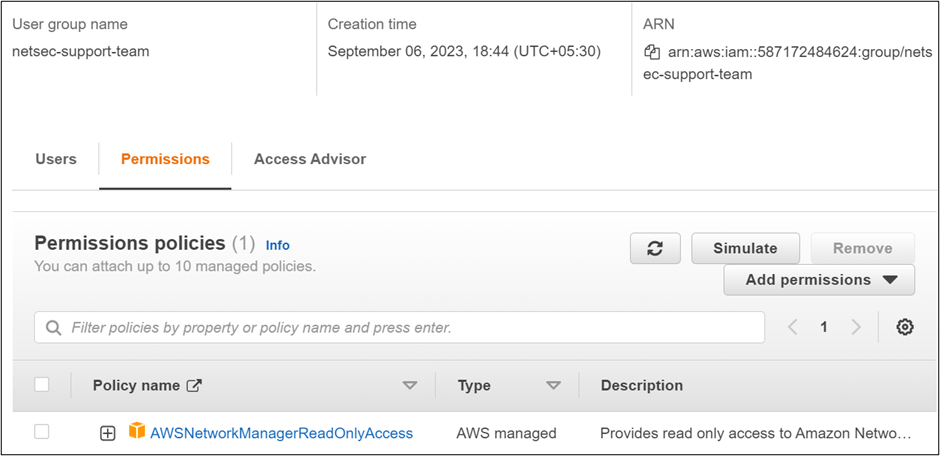 In this way, control the access to the resource and secure the environment.
In this way, control the access to the resource and secure the environment.
3. Use security groups and NACLs
Attach security groups to instances within VPCs that are connected to the Transit Gateway. This controls traffic at the instance level, allowing you to specify rules based on ports, protocols, and IP ranges.
Associate NACL with subnets connected to the Transit Gateway. NACLs help control traffic entering or leaving a subnet based on source/destination IP, port, and protocol. NACLs are useful for basic network traffic filtering, allowing you to set rules at the subnet level. They can be used for more coarse-grained control compared to security groups. For example, use NACLs to deny traffic from specific IP ranges or protocols.
Consider the organizational setup mentioned earlier. There are 3 VPCs. There is a specific requirement to block traffic from a certain IP range of instances in the subnets of VPC A from VPC B. This can be achieved by setting NACL for the subnets in VPC A and putting the IP range in the deny list. Further, the traffic from VPC B should be able to access the instances at port 443 but not at port 80. This can be set by attaching the security group to the instances where only port 443 is allowed.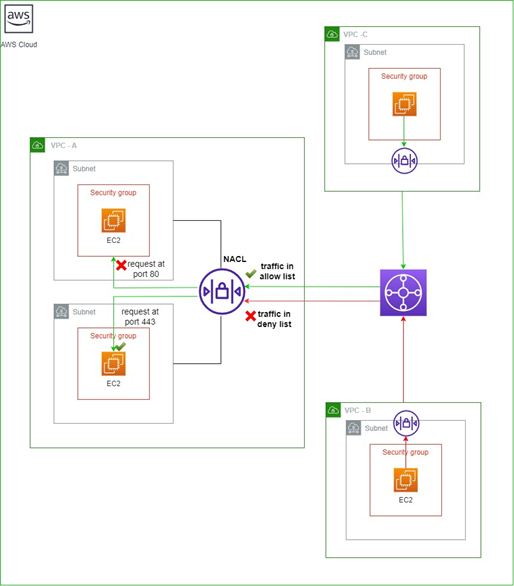
4. Filter traffic using Network Firewall with Inspection VPC
An Inspection VPC, equipped with AWS Network Firewall deployed in conjunction with a Transit Gateway, serves as a critical security checkpoint for all inbound and outbound network traffic. In this architectural design, all network traffic, regardless of its source or destination, is first routed through the Inspection VPC. AWS Network Firewall acts as the sentinel, scrutinizing each packet for security threats, filtering malicious content, and enforcing access controls in accordance with predefined security policies.
Consider a setup where there is on-premises connectivity of the AWS architecture by VPN connection. All the traffic flowing east-west or north-south can be filtered by using inspection VPC with network firewall deployed.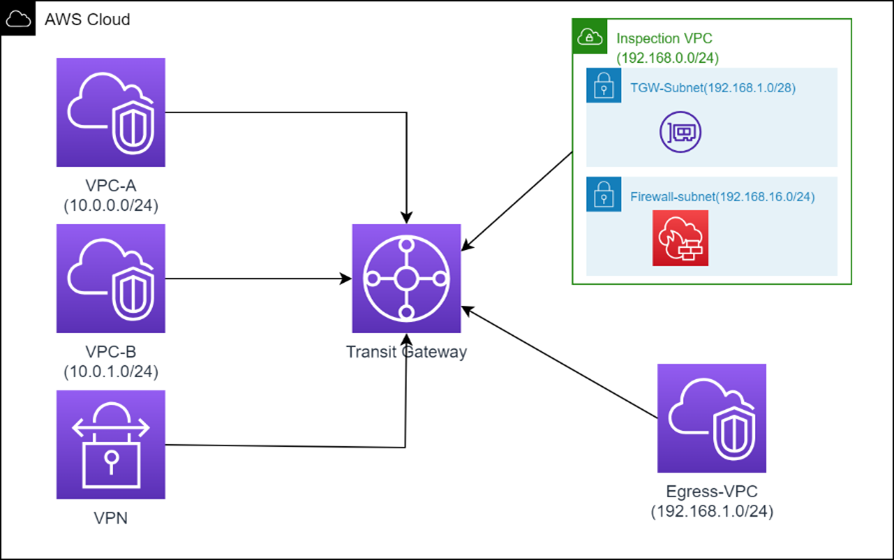
Here, there will be two transit gateway route tables.
1. Inspection Route Table:
The inspection route table will be associated with VPC A, VPC B, Egress VPC and VPN and all the traffic will go to inspection VPC.
|
Inspection Route Table |
|
|
Destination |
Target |
|
0.0.0.0/0 |
Inspection VPC attachment |
2. Direction Route Table:
This direction route table will be associated with Inspection VPC.
|
Direction Route Table |
|
|
Destination |
Target |
|
10.0.0.0/24 |
Attachment of VPC A |
|
10.0.1.0/24 |
Attachment of VPC B |
|
10.1.0.0/16 |
Attachment of VPN |
|
0.0.0.0/0 |
Attachment of Egress VPC |
The inspection VPC will have route tables that will direct the traffic filtered by Network Firewall to the VPCE (ENI) which will direct all the traffic except the internal traffic back to the transit gateway.
Challenges of using security groups:
1. Limited Scope: SGs work at the instance level and are primarily used to control inbound and outbound traffic to and from EC2 instances. They are not well-suited for controlling traffic between VPCs.
2. Lack of Centralized Control: In a multi-VPC environment, managing SGs individually for each VPC can be cumbersome. There's no centralized control point for defining and enforcing security policies consistently.
3. Complexity: In a microservices architecture or when using multiple VPCs for isolation, managing SG rules across numerous instances and VPCs can quickly become complex and error prone.
Benefits of a Centralized Firewall with Transit Gateway:
1. Centralized Control and Visibility: A centralized firewall deployed with AWS Transit Gateway serves as a single point for defining and monitoring security policies across multiple VPCs. This provides a unified and simplified approach to network security.
2. Traffic Inspection and Filtering: The centralized firewall can inspect all traffic traversing the Transit Gateway, allowing for advanced threat detection, intrusion prevention, content filtering, and the enforcement of security policies. This level of traffic inspection is beyond what SGs can offer.
3. Logging and Compliance: Centralized firewall solutions often provide robust logging and reporting capabilities, making it easier to monitor network traffic, detect security incidents, and maintain compliance with industry regulations.
Use Case
Now let us understand the multiple VPCs setup with an organization’s infrastructure hosted on AWS. To ensure compliance with stringent healthcare regulations and protect sensitive patient data, they need to establish secure connectivity between VPCs while maintaining elevated levels of security. The security measures for healthcare SaaS Platform using AWS Transit Gateway can be configured in the following way:
1. VPC-to-VPC Communication Control:
• Network Access Control Lists (NACLs) should be implemented on each VPC to limit traffic between VPCs connected to the Transit Gateway. To implement the least privilege concept, configure explicit allow/deny rules depending on source and destination IP addresses, ports, and protocols.
• Utilize Security Groups to limit communication between instances and services inside each VPC, making sure that only essential services are permitted to converse with one another.
2. Secure Routing Policies:
• Set up routing policies within the Transit Gateway to control traffic flow between VPCs. Implement explicit routes to allow communication only between designated VPCs, limiting lateral movement in case of a security breach.
• Avoid using default routes or overly permissive routing policies to minimize potential attack surfaces.
3. Data Encryption:
• For private, secure connection without using the open internet, encrypt data in transit between VPCs using AWS PrivateLink.
• To prevent unwanted access to critical information, enable SSL/TLS encryption for communication between services and apps within each VPC. ACM is a service that simplifies the process of managing SSL/TLS certificates for AWS-based applications.
4. Multi-Account Security:
• Use AWS Organizations to centrally manage multiple AWS accounts. Ensure that AWS Transit Gateway and related resources are deployed in a dedicated security account to limit access and enhance control.
• Implement AWS Resource Access Manager (RAM) to share Transit Gateway resources securely across accounts.
5. Network Monitoring and Security Analytics:
• Enable VPC Flow Logs on the Transit Gateway to capture and analyze network traffic data, facilitating detection of suspicious activities or traffic anomalies.
• Integrate Amazon GuardDuty with the Transit Gateway to automatically detect threats and intrusions, such as unauthorized port scanning or malware activity.
6. Backup and Disaster Recovery:
• Implement regular backups of Transit Gateway configurations to prevent data loss in case of unexpected incidents.
• Establish disaster recovery plans and test them periodically to ensure business continuity and minimize downtime.
The healthcare SaaS firm can use AWS Transit Gateway to establish a strong and secure multi-VPC architecture by implementing the above security measures. These procedures will support compliance, preserve the trust of healthcare organizations and patients using their platform, and safeguard sensitive patient data.
Conclusion
AWS Transit Gateway simplifies and secures multi-VPC connectivity, providing a scalable and centralized solution for inter-VPC communication. By following best practices and implementing robust security controls, organizations can build a reliable and secure network infrastructure in the AWS cloud. As organizations grow, they can expand their architecture to accommodate new VPCs and regions while maintaining an elevated level of security and performance.




