Swift and Strategic Response: Dealing with Exposed IAM Access Keys
By Bhuvaneswari Subramani / Oct 18, 2023
Introduction
If you receive an AWS abuse notice indicating that access keys have been exposed, you should take immediate action to mitigate the issue. Here's a step-by-step approach to tackle the situation:
- Verify the Notice: First, confirm the authenticity of the AWS abuse notice. Ensure that it is indeed from AWS and not a phishing attempt.
- Isolate the Affected Resources: Identify the specific resources or accounts that have been affected by the exposed access keys.
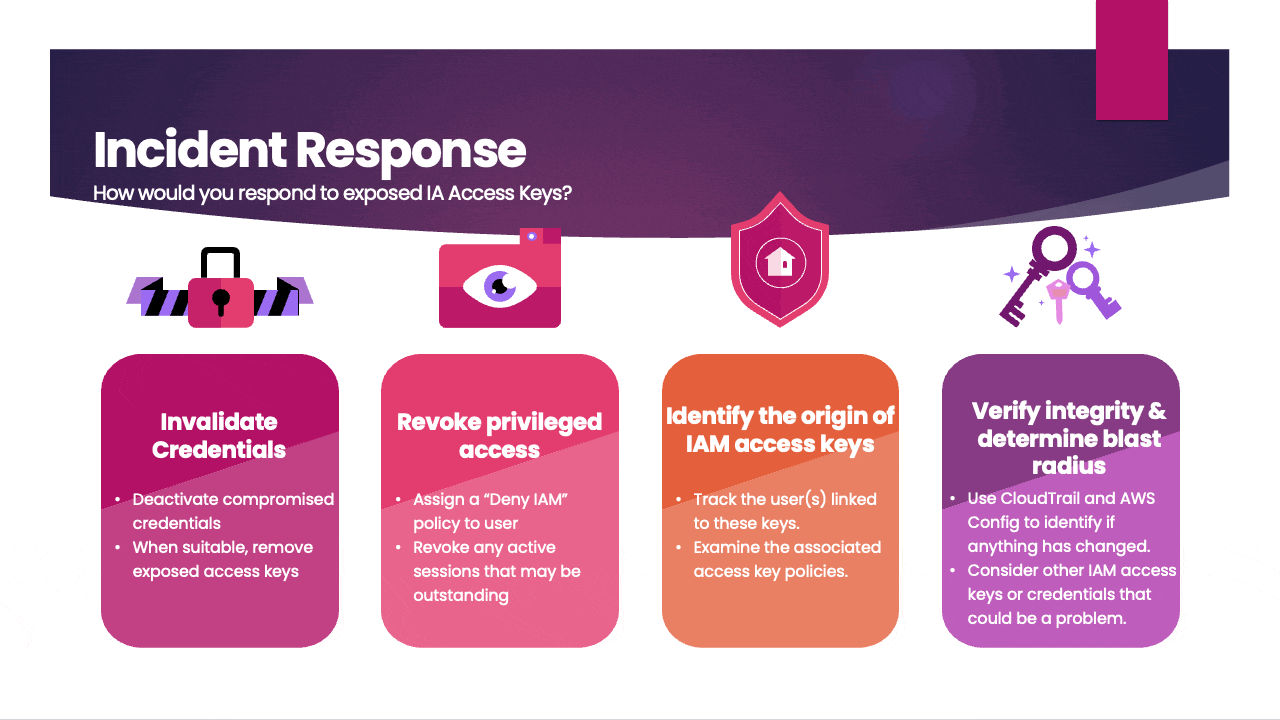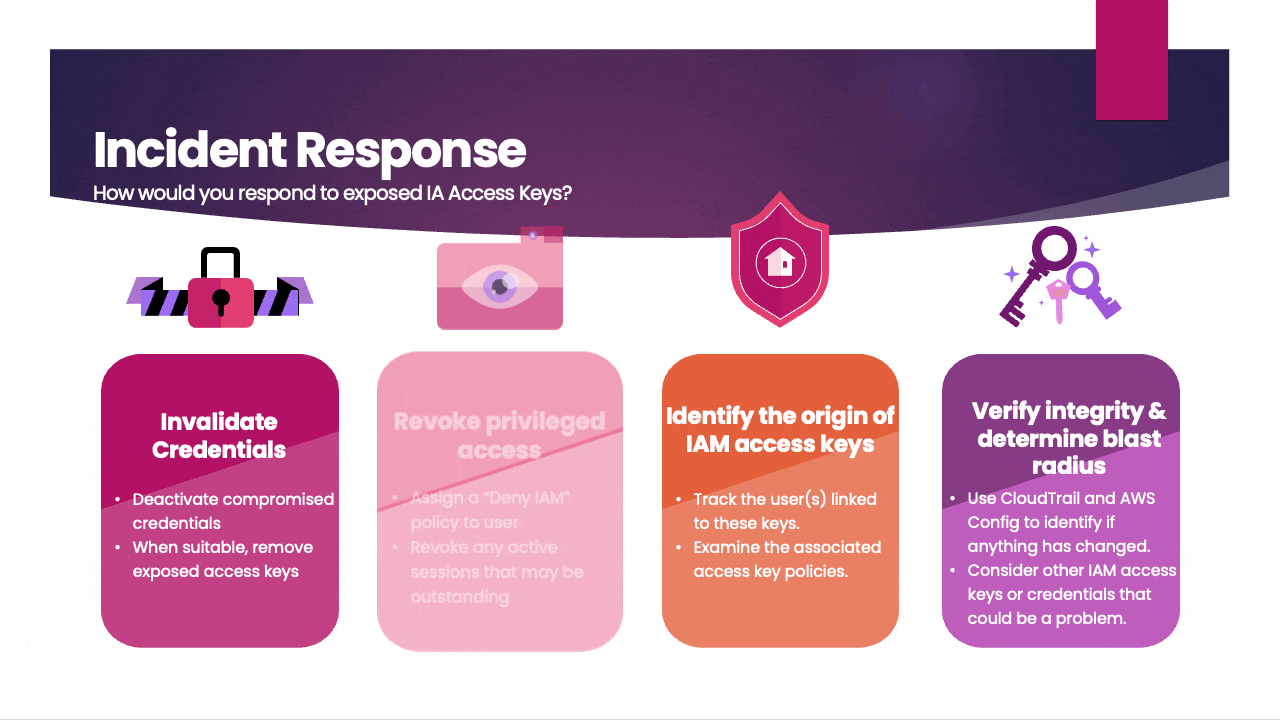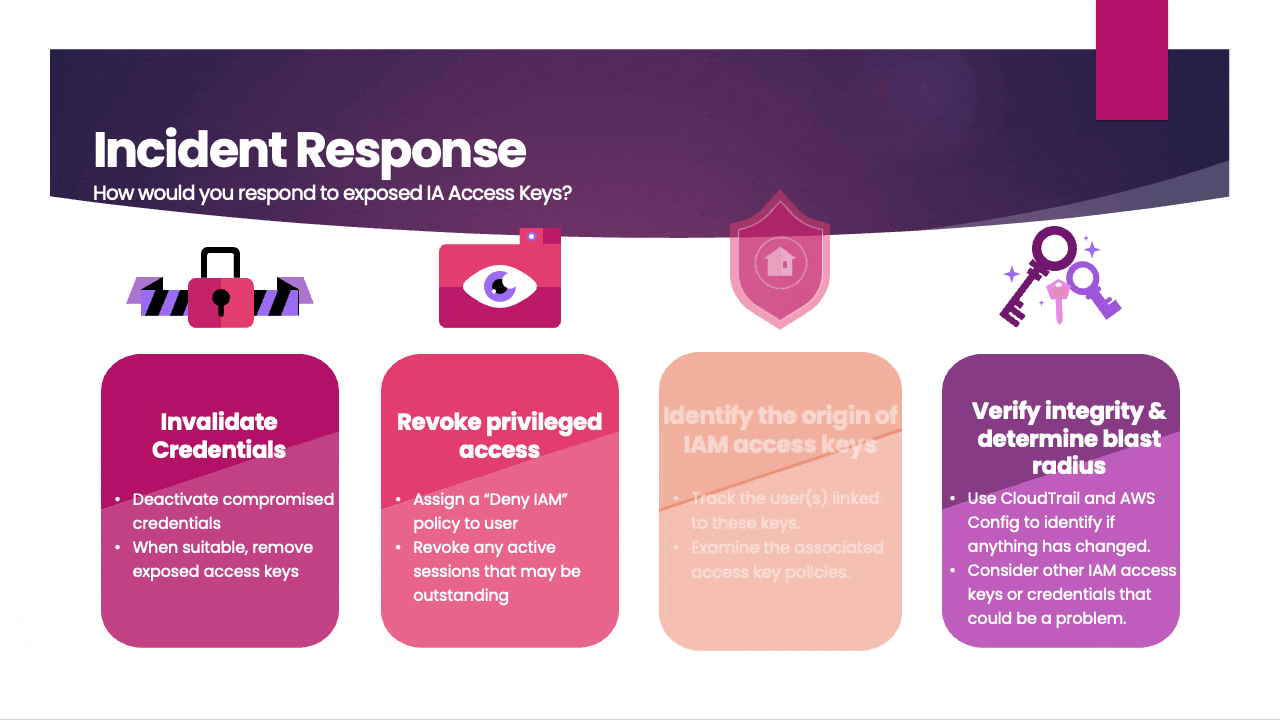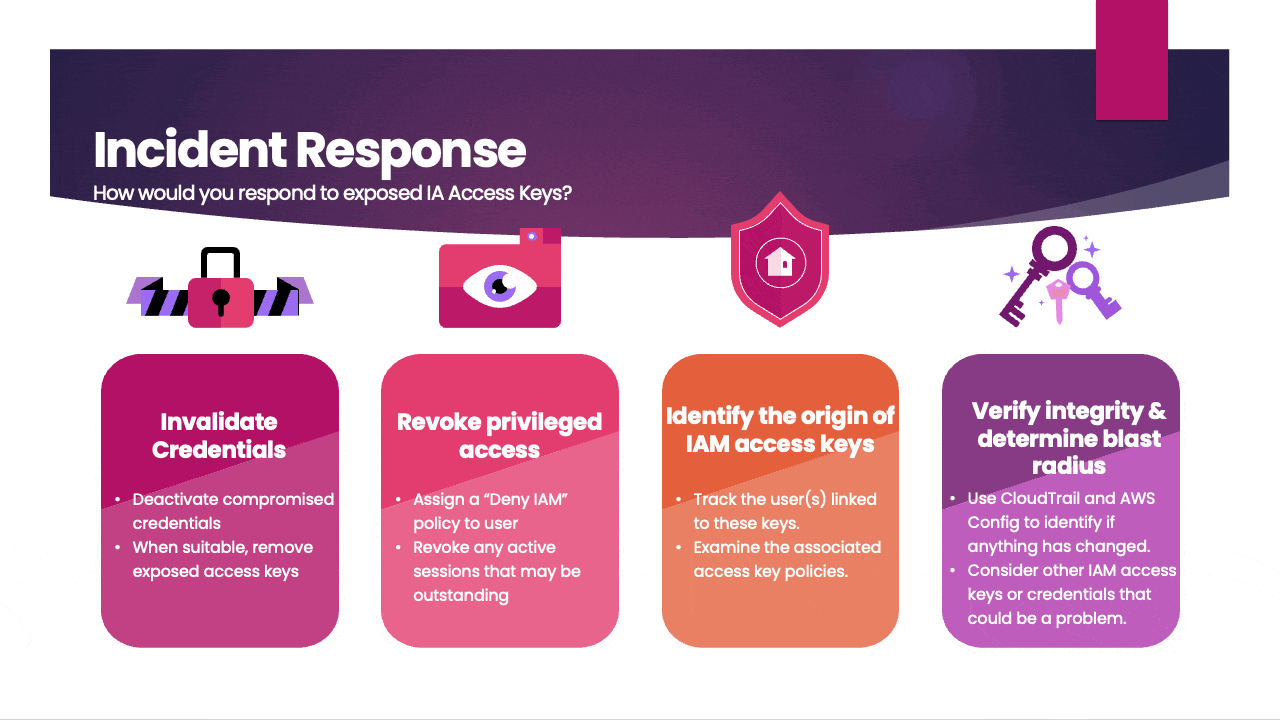
- Invalidate Credentials: Immediately deactivate or delete the exposed access keys to prevent any unauthorized access. You can do this through the AWS Management Console or by using AWS CLI commands.
- Review Access Logs: Analyze CloudTrail logs and other relevant logs to determine the extent of the exposure and whether any unauthorized actions were taken using the compromised access keys.
- Change Passwords and Rotate Keys: If necessary, change passwords and rotate access keys for the affected IAM users or roles to ensure that the compromised keys are no longer valid.
- Revoke privileged access: Assign a "Deny IAM" policy to the user to restrict access and promptly revoke any active sessions to secure the account.
- Investigate Root Cause: Determine how the access keys were exposed in the first place. It could be due to a security misconfiguration, a compromised system, or other factors. Investigate and address the root cause to prevent a recurrence.
- Verify integrity & determine blast radius: Use CloudTrail and AWS Config to identify if anything has changed. Consider other IAM access keys or credentials that could be a problem
- Implement Security Measures: Enhance your AWS security by implementing security best practices, such as enabling multi-factor authentication (MFA), regularly rotating access keys, and using IAM policies to limit permissions.
- Report Back to AWS: If you find evidence of malicious activity or a breach, report it to AWS through the appropriate channels. AWS can provide further guidance and may assist in the investigation.
- Monitor for Anomalies: Continuously monitor your AWS environment for any suspicious or unauthorized activity. Set up alarms and alerts in CloudWatch to notify you of any unusual behaviour.
- Review and Improve Security Policies: After resolving the issue, conduct a thorough review of your security policies and procedures to prevent similar incidents in the future. Consider implementing AWS Trusted Advisor to help identify security gaps.
- Educate and Train Personnel: Ensure that your team is aware of security best practices and is trained to recognize and respond to security incidents effectively.
- Documentation and Communication: Document all actions taken in response to the exposure of access keys and communicate these steps and their outcomes to relevant stakeholders within your organization.
Remember that AWS provides a range of security tools and services to help you secure your resources. Regularly reviewing and updating your security measures is crucial to maintaining a secure AWS environment.
Conclusion
In conclusion, responding to exposed AWS access keys, as prompted by an abuse notice, demands a swift and methodical approach to safeguard your cloud environment. By promptly deactivating the compromised keys, scrutinizing access logs, and implementing robust security measures, you can mitigate risks effectively. However, it doesn't end there. Continual monitoring, root cause analysis, and proactive policy enhancements are essential to fortify your AWS security posture. By adhering to these guidelines, you can turn an unsettling incident into an opportunity to strengthen your organization's resilience in the ever-evolving landscape of cloud security. Remember, preparedness and vigilance are key in navigating the complexities of cloud security.