AWS ControlTower Landing Zone Implementation
Apr 03, 2023
Introduction
The purpose of this case study is to describe how the Cloud Infrastructure team implemented an Enterprise-grade multi-account AWS Landing Zone environment for a US based Healthcare giant. This use case is aimed to improve security, governance, and control for all the existing and future accounts in the customer’s AWS Organization. The key security aspects that the Cloud Infrastructure team covered were Access-management, Preventive and Detective Security Guardrails, Governance enforcement, enabling comprehensive logging and auditing mechanisms, and iteratively evolving and improving overall governance and control.
Challenges
An Enterprise-grade multi-account AWS environment requires a strong foundational account structure and core IT services deployed for hosting the business applications and enterprise workloads. It turns a bit more complex when the legacy landing zone is implemented using a semi-automated process and tools. That was the exact scenario here with more than 15 existing AWS accounts to be enrolled on the new Landing Zone.
Here are some of the key challenges that we had to consider while designing and implementing the AWS ControlTower Landing Zone.
- AWS Account strategy aligned with the internal IT and organisational structure.
- Centralized Access and Privilege Management
- Additional Preventive Guardrails to secure critical infrastructure and meet compliance requirements.
- Migrating workload deployed in the Management Account
- Continues Security Evaluation and Traceability
- Design the network architecture
- Optimize AWS spending by streamlining billing and cost management.
- Enforce consistent governance and compliance policies across all accounts
Technology Solutions
AWS ControlTower Landing Zone Solution was designed and developed through a collaborative process with customer’s technical team. This involved conducting multiple workshops that focused on various areas, such as Network, Security, Access Management, Application and Cloud Engineering. The Landing Zone solution consisted of the following services:
- AWS Organizations - An account management service that helps to consolidate multiple AWS accounts into an organization and centrally manage them.
- AWS CloudTrail – A service that assists in enabling operational and risk auditing, governance, and compliance of the AWS account
- AWS Config- A service that helps assess, audit, and evaluate the configurations and relationships of the AWS resources.
- Guardrails- Preventive and Detective Guardrails, also known as controls, are broad guidelines that offer constant governance for your entire AWS environment. They are the law enforcers in an AWS environment.
- AWS SSO- It is one of the most efficient, secure, and effective single sign-on services now known as an AWS IAM Identity Center.
- Centralized Terraform Tooling to provision AWS resources in any account using Terraform Templates
- Region restrictions was configured to allow 2 regions
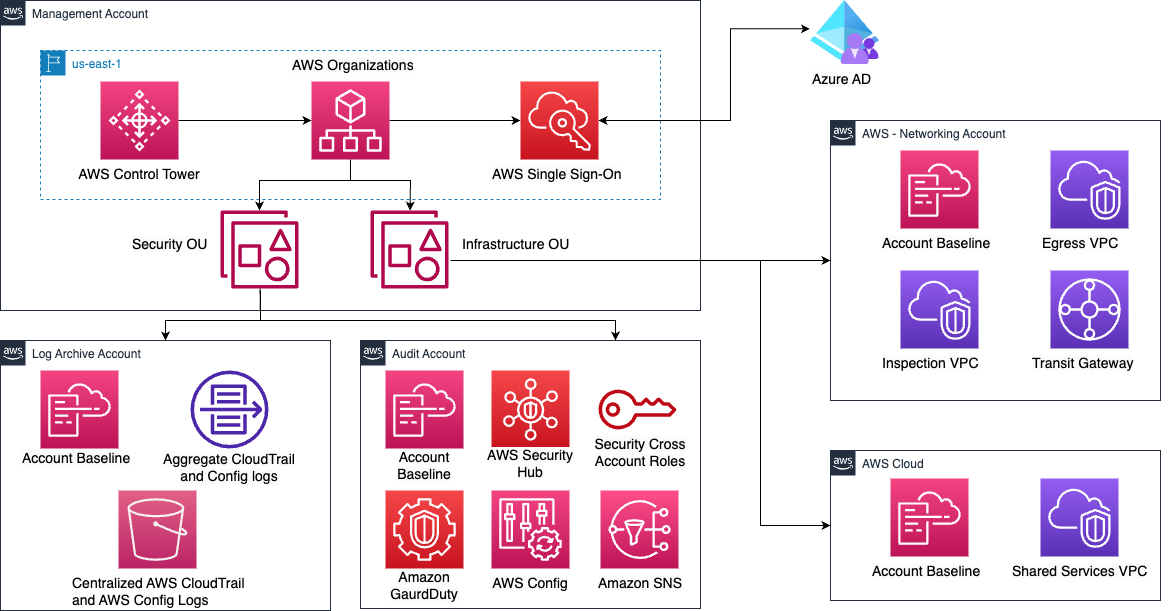
These services help set up a secure baseline for all the current as well as the future AWS Accounts. To meet additional security and governance requirements of the customer, Intuitive.Cloud enabled the following native AWS Security Services
- AWS SecurityHub
- AWS GuardDuty
AWS Control Tower's landing zone provides guidance on industry-standard best practices and offers pre-configured blueprints for identity management, federated access, and account structure. These blueprints serve as templates that can be easily implemented on AWS Control Tower.
Among the blueprints that are available on AWS Control Tower are:
- A multi-account environment using AWS Organizations
- Cross-account security audits using AWS Identity and Access Management (IAM) and AWS IAM Identity Center (successor to AWS Single Sign-On)
- Centralized logging from AWS CloudTrail, and AWS Config stored in Amazon Simple Storage Service (Amazon S3)
- Preventive guardrails are implemented using service control policies (SCPs), which are a part of AWS Organizations. Detective guardrails are implemented using AWS Config Rules and AWS Lambda functions.
Example:- Ensures tagging standards with relevant metadata
- Disallow public write-access to the S3 bucket
- Enforce a strong password policy and rotate them regularly
- Enforce VPC security, such as restricting public access and implementing network ACLs and security groups
- Ensures EBS volumes are encrypted to protect data at rest
- Disallow unattached EBS volumes
A centralized inspection VPC (Virtual Private Cloud) was deployed to inspect the ingress and egress traffic using Palo-Alto firewall.
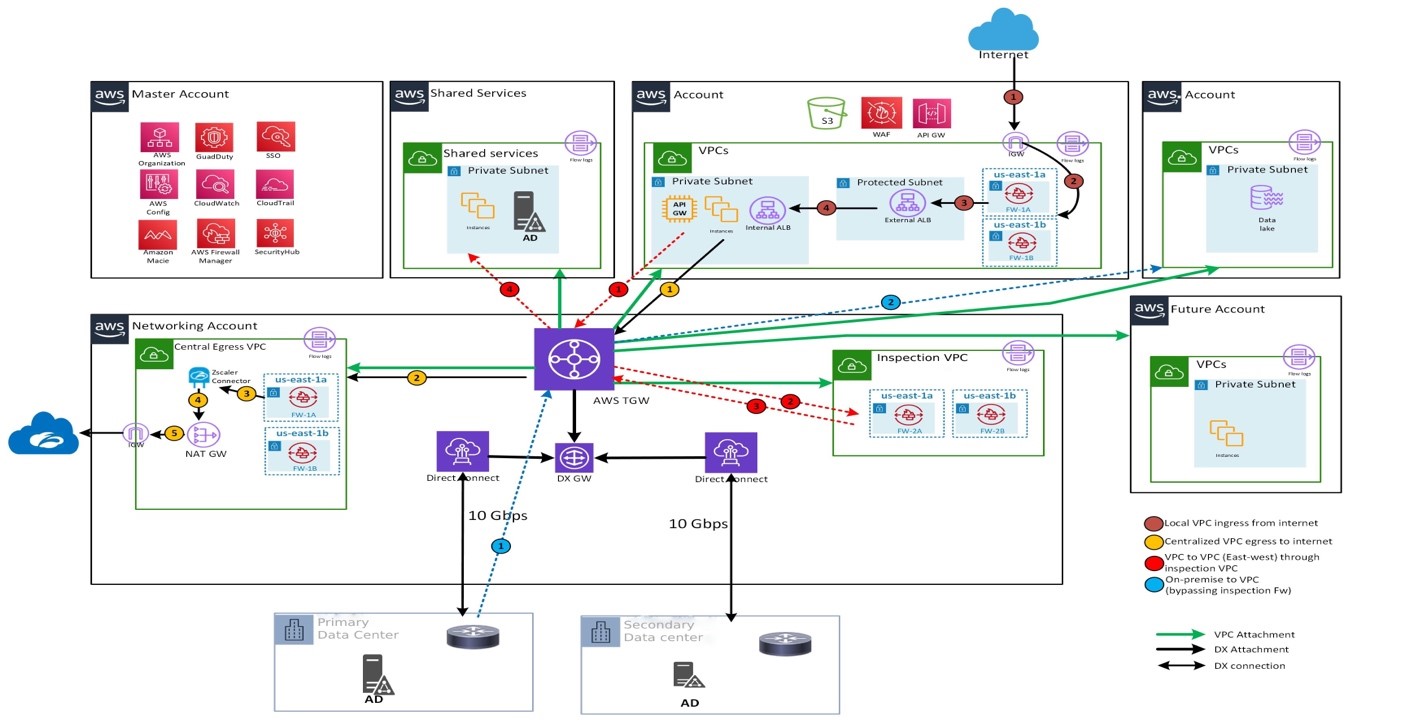
Implementation Strategy
After assessing the client’s environment and thoroughly understanding their requirements the Intuitive.Cloud Engineering team deployed the entire Landing Zone solution using Terraform
- Created the AWS Organizational Unit (OU) and account structure
- Integrated Amazon SSO with Client’s on-premises AD.
- Deployed the core Landing Zone using AWS Control Tower
- Centralized Terraform tooling to enable infrastructure provisioning across all the AWS Accounts.
- Enabled AWS SecurityHub and GuardDuty - delegated Admin as the “Audit” account
- Implemented custom Guardrails to improve the security posture.
- Created centralized S3 storage .
- Hub and Spoke connectivity model using Direct Connect and Transit Gateway
- Inspection VPC (Virtual Private Cloud) was deployed to inspect the ingress and egress traffic using Palo-Alto firewall
- Enrolled all the existing accounts in a controlled manner
- Cloud ultimately provided the customer with a thorough engineering design that encompassed runbooks, platform designs and configurations, and a detailed knowledge transfer plan for both the business and technology teams.
Results and Impact
After the successful deployment of the Landing Zone solution, the customer observed the following benefits:
- Centralized Access and Privilege management for their accounts
- Organizational policy and compliance enforcement across all the accounts helped enhance their overall compliance and governance aspects
- Centralized logging and visibility of audit logs and network logs provided better visibility and control over their resource and their access.
- Centralized toolchain for infrastructure provisioning using terraform
- Ability to iteratively evolve and improve their overall governance and control across all the AWS accounts
- Standard tagging for all resources helped them with cost allocation, resource tracking, and security monitoring.
- AWS's global network with multi-region setup was used to achieve fast and reliable
- To achieve low latency for end-users
- To extend resilience to handle regional outages (partial or total)
- Disaster recovery setup to extending our resiliency to handle partial or complete regional outages.
- To meet business requirements to store data in distinct regions, separated by several hundreds of miles.
Conclusion
To summarize, the Healthcare customer encountered various governance and security-related challenges while working with their legacy landing zone. However, through close collaboration with Intuitive.Cloud, they were able to enhance their multi-account Landing Zone infrastructure, achieving improved visibility and governance over their resources. As a result, the customer was able to establish a robust, secure and compliant AWS environment, enabling them to accelerate their cloud adoption efforts.




