Building a Secure, Scalable, and Resilient Cloud Infrastructure to Support CoreBT's Payment Services
May 07,2025
Contents
1. Executive Summary
This case study details the implementation of a secure and scalable multi-account AWS environment using AWS Control Tower to modernize the organization’s cloud infrastructure for its critical payment services. By establishing a Control Tower Landing Zone, the organization has created an organized architecture that enables governance and compliance with customized Organizational Units (OUs) & Service Control Policies (SCPs). This included an Inspection VPC with Palo Alto firewalls for packets traffic monitoring to provide strong security against threats. This included adapting guardrails to meet the specific needs of different organizations, handling policy drift and shifting security infrastructure without sacrificing performance. In summary, the deployment greatly improved cloud governance and security posture for this organization while enabling operations to be more efficient as well; resulting in a dynamically capable infrastructure that can change gears with changing business demands.
2. About the Customer
CORE Business Technologies is an end-to-end solution provider specializing in payment solutions, revenue management, and customer engagement. The company focuses on delivering modern and convenient experiences through its scalable solutions, catering to public sector, government, and higher education organizations.
3. Introduction
Project Overview: CoreBT undertook a cloud migration strategy to modernize its payment services platform by deploying its infrastructure into AWS. The Control Tower Landing Zone was implemented to manage multiple AWS accounts securely, ensuring scalability, compliance, and centralized monitoring. Also a comprehensive database migration to Amazon RDS was undertaken to ensure improved security, scalability, and operational efficiency.
Objectives:- Establish a scalable, secure multi-account AWS environment.
- Centralize network routing and security through AWS Control Tower.
- Implement Service Control Policies (SCPs) to enforce governance across accounts.
- Implement Amazon RDS to improve database security and performance.
- Ensure encryption for data at rest and in transit.
- Implement an effective Disaster Recovery (DR) solution
4. CoreBT AWS Landing Zone Setup
Landing Zone Architecture: The AWS Landing Zone was deployed using Control Tower in a multi-account structure. The management account hosts the central Control Tower, while separate Organizational Units (OUs) were created for workloads, security, and shared services.
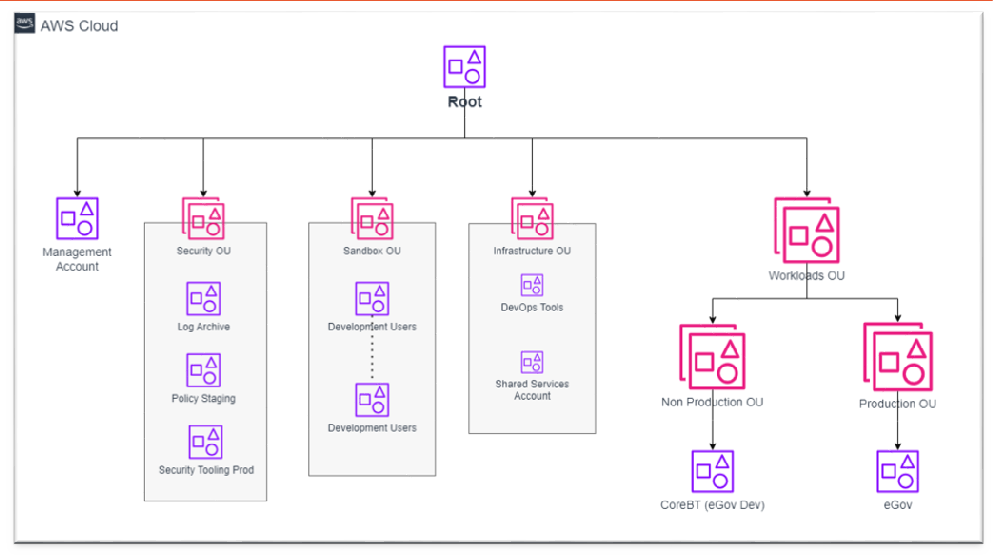
- Management Account: Centralized billing and account creation.
- Sandbox OU: Used for testing services and tools.
- Security OU: Includes log archive and audit accounts.
- Infrastructure OU: Centralized shared services and network.
- Workloads OU: Segregated for production and non-production environments.
Service Control Policies (SCPs): SCPs were applied to enforce governance, restricting unnecessary actions and securing workloads. Key policies prevented changes in sensitive environments and restricted direct internet access from workload accounts.
5.Control Tower Architecture Components
AWS Organizations and Control Tower Setup: Control Tower was integrated with AWS Organizations to manage all accounts under a centralized management account. AWS Control Tower guardrails provided both preventative and detective controls.
Account Management: Control Tower provided lifecycle management, creating and configuring new AWS accounts within pre-defined guardrails, ensuring compliance with CoreBT’s security standards.
OU Design and Guardrails: Each OU had specific guardrails in place to manage security, compliance, and resource management. Detective and preventative guardrails, such as enabling CloudTrail logs and AWS Config rules, were configured to monitor account activity
6. Security and Compliance
Log Archiving and Security Tooling: A centralized log-archive account was created to store security logs across all accounts. Security services such as GuardDuty and Security Hub were integrated to ensure consistent monitoring of the AWS environment.
Security Services Integration: GuardDuty and Security Hub were deployed to detect and monitor threats across all accounts. AWS Config provided a detailed view of resource compliance with defined guardrails.
Identity and Access Management: IAM roles were centrally managed, allowing granular access control across accounts. AWS IAM Identity Center was deployed for Single Sign-On (SSO), enhancing security and simplifying access to multiple AWS accounts.
7. Infrastructure as Code (IaC)
Terraform Automation for Landing Zone: All subsequent infrastructure components, such as security, network configurations, and workload management, were automated using Terraform. This ensured that the architecture remained scalable and easily manageable while adhering to the policies set by the Control Tower
Terraform for Resource Management: Post-deployment, Terraform was used extensively to manage the infrastructure across different AWS accounts and organizational units. This included:
- Managing VPCs, subnets, and security groups across the environment.
- Automating the setup of application load balancers, EC2 instances, RDS databases, and other cloud resources.
- Enabling centralized logging, monitoring, and security tools such as AWS Security Hub and GuardDuty to be consistently deployed across all accounts
Scalability and Flexibility: With Terraform managing these components, CoreBT achieved a high level of flexibility and could scale resources efficiently based on evolving business needs without manual intervention
8. Database Migration Strategy
Architecture Diagram:

The AWS architecture was designed to meet scalability, security, and operational requirements. The infrastructure includes:
Network Design:
- Route 53 for DNS routing with latency-based routing to ensure optimal performance.
- Security VPC with public subnets containing NAT gateways, firewall instances for traffic filtering, and Web Application Firewall (WAF) for added protection.
- Transit Gateway for secure inter-VPC communication, improving scalability and connectivity.
Application Architecture:
- Web App VPC with redundant web app instances in different availability zones for fault tolerance.
- Application Load Balancer (ALB) for distributing incoming traffic across web instances.
- Batch Jobs EC2 instances to handle intensive data processing workloads.
- RDS MySQL with primary and replica instances for high availability and improved performance.
- AWS Transfer Family configured for secure and efficient SFTP data transfers with granular permission controls.
Security Enhancements:
- AWS WAF implemented for web application security.
- Security VPC firewalls configured to restrict unauthorized access.
- PCI-DSS security controls integrated into the infrastructure.
Migration Strategy
The migration strategy included:
- AWS DMS (Database Migration Service) was used to perform a full load followed by continuous data capture (CDC) replication for minimal downtime migration.
- Batch jobs were created for scheduled data synchronization to ensure data consistency during cutover.
- The migration involved truncating tables in the source database and rerunning the DMS full load task followed by CDC replication.
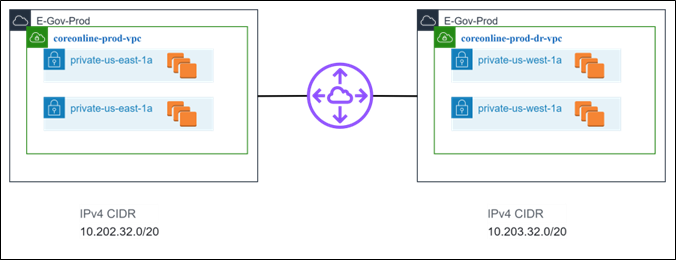
Disaster Recovery (DR) Setup
A robust DR plan was established to ensure business continuity:
- Multi-AZ RDS replication for database failover.
- Cross-region backups to ensure data availability.
- Automated recovery scripts for infrastructure restoration.
- The DR setup achieved an RPO of 15 minutes and an RTO of 4 hours, ensuring minimal data loss and swift recovery.
Application Cutover and Post-Migration Validation
- A detailed cutover plan was followed, including:
- Putting client applications into maintenance mode.
- Running DMS full load tasks for temporary tables.
- Executing final data synchronization jobs.
- Switching DNS records to point to the new RDS endpoints.
- Rollback strategies were defined to address potential issues during the cutover process. These included:
- Maintaining backups of the source database prior to cutover.
- Creating manual snapshots of the RDS instance at key stages.
- Keeping source database instances available in read-only mode as a fallback mechanism.
- Post-migration testing was conducted using both host file entries and live DNS to ensure application stability.
9. Customer Challenges and Solutions
Challenge: Control Tower’s default Service Control Policies (SCPs) sometimes restricted critical services needed by CoreBT’s workloads.
Solution: SCPs were customized to balance security while allowing essential services to function properly.
Challenge: As new accounts and resources were added, ensuring continuous compliance with Control Tower’s policies was difficult.
Solution: Regular audits and automated checks were implemented to monitor and correct policy drift.
Challenge: Deploying an Inspection VPC with Palo Alto firewalls to secure east-west and north-south traffic across VPCs, while ensuring minimal impact on network latency and performance.
Solution: The Inspection VPC was designed with AWS Gateway Load Balancer (GWLB) and Palo Alto firewalls, ensuring high availability and scalability. Traffic was routed efficiently through AWS Transit Gateway, enabling centralized security inspection without compromising network performance
Challenge: Ensuring minimal downtime during database migration while maintaining data consistency.
Solution: AWS DMS with CDC replication was implemented to continuously sync changes from the source database to the target RDS instance, reducing downtime during the cutover.
Challenge: Implementing secure database connectivity across regions for DR readiness.
Solution: VPC peering and static routing were configured to ensure secure and seamless connectivity between primary and DR regions.
10. Results and Outcomes
By leveraging Control Tower, CoreBT was able to enforce guardrails that ensured consistent security and compliance across accounts. Automation through Terraform also reduced the operational overhead involved in manual provisioning.
The centralized architecture reduced operational costs by eliminating the need for individual security setups in each account. AWS Transit Gateway provided centralized routing, reducing the complexity and cost associated with managing multiple VPC connections.
Enhanced database security with comprehensive encryption, IAM role enforcement, and MFA integration.
Reduced downtime and improved data consistency via CDC replication during migration.
Enhanced disaster recovery readiness with improved RPO and RTO metrics.
11. Conclusion
This case study demonstrates how AWS Control Tower helped CoreBT establish a resilient Landing Zone, ensuring governance, security, and scalability across its AWS accounts. Additionally, the successful RDS migration provided CoreBT with a secure, scalable, and managed database solution in alignment with AWS best practices. This ensured operational efficiency while strengthening CoreBT's security posture and improving disaster recovery capabilities.




